CIRRUS Dark Web Monitoring
Track and identify sensitive information that may have leaked into the dark web.Why Dark Web Monitoring Matters
Dark web monitoring helps protect your business by identifying exposed data before it can be exploited. Below are the key benefits and value propositions of incorporating dark web monitoring into your cybersecurity strategy.
Early Detection
Identify compromised credentials and sensitive information before hackers can exploit them.
Reduce Manual Effort
We handle the monitoring, allowing you to focus on daily operations while staying protected.
Protect Your Reputation
Prevent public breaches and keep your organization out of damaging headlines.
Enhanced Security
Receive actionable insights to strengthen your security protocols, change passwords, and update defenses as soon as threats are detected.
How CIRRUS Protects You
When it Comes to Dark Web Monitoring
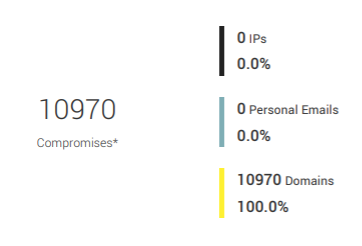
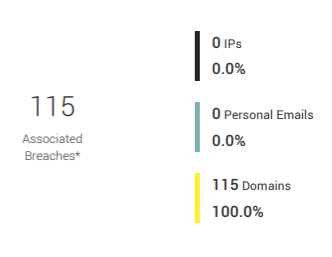
24/7/365 Monitoring
Continuous scanning of the dark web for any data leaks associated with your domain, including email addresses, passwords, and financial information.
Real-Time Alerts
Be instantly notified when new breaches are detected, allowing for immediate action.
Comprehensive Reports
Receive detailed reports outlining all compromised data, with recommendations to mitigate risks.
Supply Chain Security
Monitor third-party vendors and partners to ensure security beyond your organization.
Trending Resources
By Anthony Siravo Why Every Organization Needs a Formal Cybersecurity Program Across industries, security failures rarely stem from a lack […]
By Shaun Babula Over the past several years, many SMB IT leaders have been encouraged to pursue a “best-of-breed” approach […]
By Jason Zanetti In the world of cybersecurity, the terms “penetration testing” and “vulnerability scanning” are often used interchangeably. However, […]
By Shaun Babula As cyber threats continue to evolve, businesses in regulated industries face increasing pressure to safeguard sensitive data […]
By David Dlug After 15 years in the technology space, we’ve seen firsthand how quickly the landscape can shift, from […]
By Jason Zanetti Patch management is often viewed as a routine task, one that organizations sometimes overlook or delay in […]
By Will Colleran The shift to remote work has transformed the way organizations operate, but it has also introduced unique […]
By Shaun Babula As cyberattacks become more sophisticated and frequent, many organizations are turning to Managed Detection and Response (MDR) […]